KAPE has seen a number of key updates during the first quarter of this year. Our team of experts has put together the below guide of all the important changes since January 2021.
Key KAPE Updates
- Documentation for KAPE Targets and Modules have been standardized
- KAPE Target Guides and Templates as well as Compound Target Guides and Templates have been created
- SQLECmd has been added as a Module that can be utilized when seeking to parse SQLite databases with both consistent and inconsistent naming conventions
- KapeResearch Modules have been developed to help automate conversion to XML (EVTX Files) or JSON (Registry Hives) for purpose of creating or updating EvtxECmd Maps and RECmd Batch Files
- Sync Modules have been developed, including: Sync_KAPE.mkape, Sync_EvtxECmd.mkape, Sync_RECmd.mkape and Sync_SQLECmd.mkape
- KAPE.exe 1.0.0.0 was released with the ability to use presigned URLs with AWS S3
Use !!ToolSync to make sure KAPE's Targets and Modules are up to date:
See end of the article for additional updates.
Standardization of KAPE Targets and Modules
KAPE Targets and Modules were standardized earlier this year to a template that includes documentation for each artifact to which a Target or Module relates. Now, when you open a Target or Module into a text editor and learn where the artifact resides, .tkape and .mkape files will outline what documentation (if any) exists for the artifact, and what guidance the author has provided for using the Target and/or Module. These can also be opened within gKape by double clicking on a Target or Module where they can be viewed and edited, if needed, prior to execution.
Update of select Targets and Modules
The !BasicCollection and KapeTriage Targets were updated to better reflect the needs of those who use those Targets in their everyday work. !BasicCollection no longer pulls $R files AND $I files from the recycle bin, rather, only $I files are pulled due to a much smaller footprint, comparatively. KapeTriage added the Windows Timeline artifact (parses with WxTCmd) and the PowerShellConsole artifact. Every tool within the !EZParser Module will be put to use so long as the artifact(s) exist in the data collected.
The !EZParser Module was updated to include two of Eric Zimmerman’s newer tools: SQLECmd and SumECmd. It is important to pay particular attention to the SQLECmd repository as there are Maps, similar to EvtxECmd, that are constantly being created and updated. Our experts recommend watching that repository to remain up to date with new updates to sync and benefit from the work of others.
Part of the update process has now been automated by way of a KAPE Module. The !!ToolSync moduleautomates the sync feature for KAPE (Targets/Modules), EvtxECmd (Maps), SQLECmd (Maps) and RECmd (Batch Files). Running this module along with a normal workflow while connected to the internet, will update the local files from each respective GitHub repository to ensure you have access to the most up to date versions prior to parsing with those tools.
SQLECmd
SQLECmd is a tool that has a matured a lot recently due to new Maps being added for iOS, Android and Windows. Maps are continuously being built for artifacts that cover mobile and desktop operating systems. Any SQLite database, regardless of source, can be parsed with SQLECmd so long as a Map exists for the database schema. Additionally, SQLECmd can be used as a validation tool for mobile forensics to validate the output of commercial vendor tools as well as conducting primary analysis on any databases extracted from a mobile device. For Windows, multiple web browser databases now have Maps which allow for those databases to generate CSV output based off the SQL Queries within those Maps. SQLECmd allows you to control the output of the data in the database, from CSV column names, column order, linking of tables and more.
RECmd
The last important highlight is related to RECmd. RECmd utilizes Batch Files as a means to filter out the parts of the Registry that aren’t useful to the end examiner. Much of the Registry offers very little of use to a forensic examiner, but for the parts that are of interest, a Batch File can be curated to exploit those artifacts and output them into a standardized CSV when using the Batch switch with RECmd. Modules have been created for KAPE to call upon each of the Batch Files. Additionally, a new Batch File was put together called the Kroll Batch File. This Batch File builds upon the others and was created to serve as an educational resource by incorporating documentation with each artifact as well as verbose comments that will reside in the Comments column of the CSV output to help the examiner better understand each artifact. It may be helpful for those looking to learn more about the Registry to view the Kroll Batch File in a text editor and dive into the documentation of the artifacts to further strengthen your knowledge of the Registry.
For anyone looking to learn more about digital forensics, develop a better workflow or become more comfortable with the command line and CSVs rather than GUIs, our experts strongly recommend running KAPE on their own systems. Start with either !BasicCollection or KapeTriage for Targets and !EZParser for Modules. Examine the output in Timeline Explorer, another tool created by Eric, and learn what and how your systems records artifacts.
Here is an overview of all KAPE changes from January 1, 2021 to March 31, 2021.
Targets that have been added/updated
- Antivirus.tkape: added SecureAge.tkape
- CloudStorage.tkape: updated Google Drive and Dropbox artifacts
- IrfanView.tkape
- Microsoft Apps: MicrosoftOneNote.tkape, MicrosoftToDo.tkape
- OpenSSH: OpenSSHClient.tkape, OpenSSHServer.tkape
- HeidiSQL.tkape
- MediaMonkey.tkape
- Signal.tkape
- SQLDatabases.tkape: Every SQLite database known to KAPE Targets will be aggregated here moving forward to be used in conjunction with the SQLECmd Modules
- SumatraPDF.tkape
- TreeSize.tkape
- WebBrowsers.tkape: Updated artifacts for Chrome and Firefox
- Windows and WindowsOSUpgradeArtifacts.tkape
Modules that have been added/updated
- MFTECmd_$MFT_FileListing: Created in order to utilize the --fl switch to create a File Listing
- RECmd Batch File Modules: developed for each Batch File
- SumECmd.mkape
- !EZParser: added SumECmd and SQLECmd
Important GitHub Repositories
Our experts recommend “watching” the following GitHub repositories for KAPE-related updates:
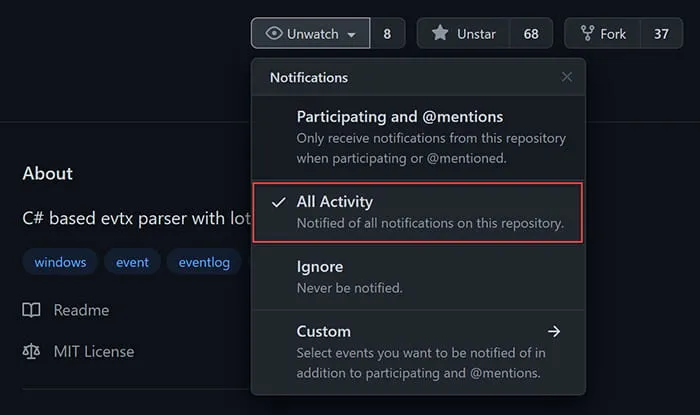
- https://github.com/EricZimmerman/KapeFiles - KAPE Targets and Modules
- https://github.com/EricZimmerman/RegistryPlugins - Registry Explorer/RECmd Plugins
- https://github.com/EricZimmerman/RECmd - RECmd Batch Files
- https://github.com/EricZimmerman/SQLECmd - SQLECmd Maps
- https://github.com/EricZimmerman/evtx - EvtxECmd Maps
- https://github.com/EricZimmerman?tab=repositories - All of Eric Zimmerman’s GitHub repositories
If you need additional KAPE support, explore our virtual live training and certification opportunities or contact our experts at Kape@kroll.com. An enterprise license is required when KAPE is used on a third-party network and/or as part of a paid engagement.
This article was written by Andrew Rathbun, a Senior Associate in Kroll's Cyber Risk practice.