Microsoft 365 (M365) has become the industry standard for business email platforms, allowing users access to a variety of interconnected productivity and communication applications. With data readily available across multiple applications within M365, threat actors are using a specific technique to exfiltrate data within a user’s M365 email account.
For the past year, Kroll has noticed an uptick of threat actors gaining unauthorized access to an M365 email account and installing legitimate third-party applications, such as PerfectData, to download a full copy of the victim’s mailbox. When threat actors use this type of technique on email accounts that contain sensitive information, the results can be extremely damaging to a company’s operations and reputation.
Attack Vector
Adversary-in-the-middle (AiTM) has become a common business email compromise (BEC) attack vector. AiTM is a sophisticated attack that begins with a phishing email sent by the threat actor to their intended victim. The phishing email typically contains a link to a fake login page that mimics an M365 login page. This fake login page is hosted by a proxy server that the threat actor controls. The proxy server is simply a computer that acts as a threat actor-controlled bridge between the victim and a legitimate authentication service. Its purpose is to capture and forward requests and responses between the two.
When a victim receives a phishing email and clicks on the link, they are redirected to a fake M365 login page. The victim will then enter their username and password which is captured by the proxy server and then forwarded to the legitimate authentication service. If multifactor authentication (MFA) is configured, the victim is prompted to satisfy the MFA requirement as expected during a normal login. Just as with the username and password, the proxy server captures and forwards the MFA token to the legitimate authentication service. The result is a successful login authentication, along with a valid session token, which is passed back through the proxy server. The threat actor is then able to hijack the existing, authenticated M365 session and access the victim’s mailbox.
By default, M365 session tokens are active for 90 days or until the session is revoked or the user’s password is changed. This default setting allows the threat actor to maintain a presence within M365 mailboxes for up to 90 days.
Additional Persistence Technique
After a threat actor has gained access to an M365 email account, an additional measure can be taken by the threat actor to maintain unauthorized access. By adding an alternative phone number or registering an additional device to the victim’s MFA, a threat actor can sign into the victim’s email account using the victim’s credentials and, when prompted, the threat actor can satisfy MFA using the alternative phone number or registered device. Threat actors typically evade detection by the victim because to view any alternative MFA configurations, the user must choose “Sign in another way” on the login page (Figure 1). This option is often overlooked or disregarded by victims, as they use their primary MFA device to authenticate.
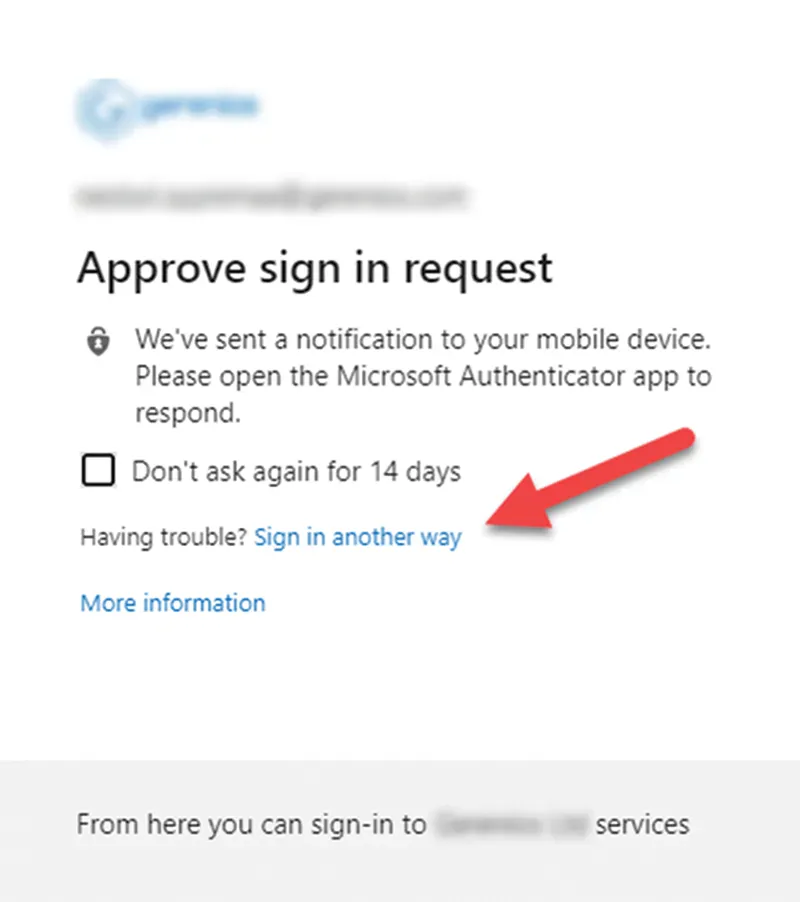
Figure 1 – Alternative MFA Options
Unlike stealing session tokens, a threat actor can satisfy MFA multiple times with this method and continue to maintain unauthorized access to the M365 email account.
Enterprise Application Abuse to Exfiltrate Mailbox Data
Once a threat actor has gained access to a victim’s M365 mailbox, Kroll typically sees evidence of the threat actor installing legitimate, third-party applications to exfiltrate user data. One of the most common applications threat actors abuse is PerfectData. PerfectData is a legitimate software that will backup email messages from cloud-based services, such as M365, to a local computer. By default, as soon as an email account is authenticated in PerfectData and a destination location is verified, the mailbox contents will begin to back up the mailbox data to the specified destination location. The threat actor then has a full copy of the victim’s mailbox.
Identification of Malicious Enterprise Applications
Two methods can be used to check for installation of third-party applications.
The first method is to review currently installed enterprise applications in the M365 Azure portal. By navigating to Microsoft Entra ID and then Enterprise Applications, one can view a full listing of available applications. For an application such as PerfectData, an application ID of ff8d92dc-3d82-41d6-bcbd-b9174d163620 will display along with the name of the application and the date the application was first observed.
The second method is to review the Unified Audit Logs within the Microsoft Purview portal. Kroll recommends creating a search across all user accounts for the following operations that are related to enterprise application usage: Consent to application, Add app role assignment grant to user, Update application and Add app role assignment to service principal. The resulting audit data will contain details regarding the application name and ID and can quickly identify the presence of an unexpected application, such as PerfectData.
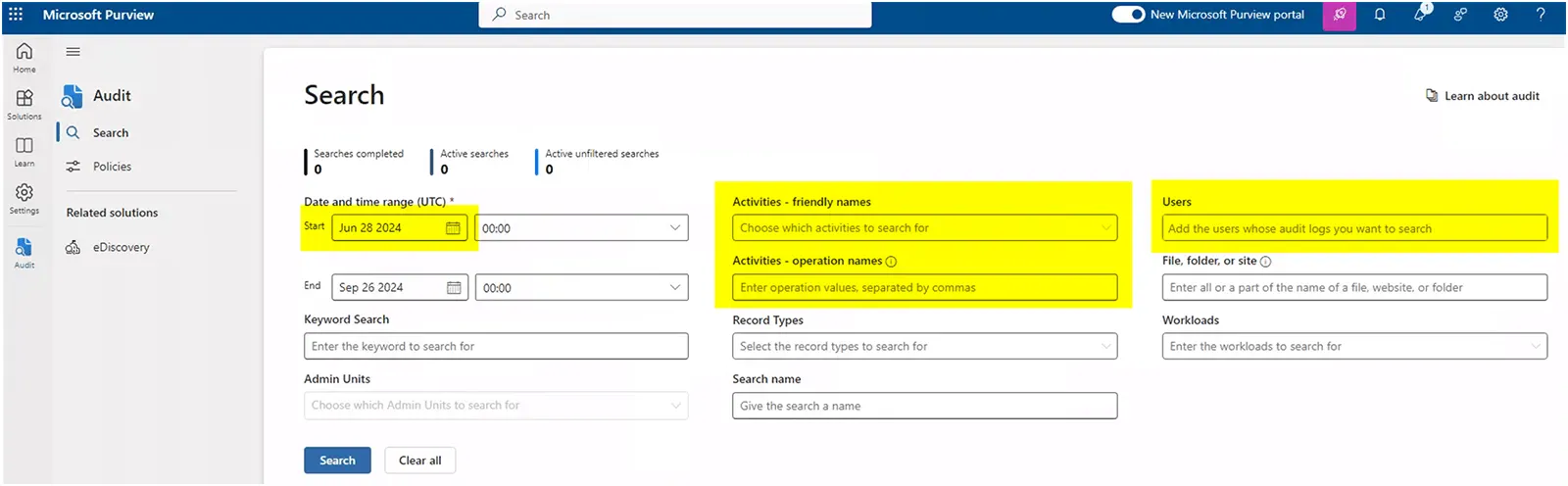
Figure 2 – Microsoft Purview Unified Audit Log Parameters
Remediation
If an enterprise application such as PerfectData is identified and deemed malicious within an M365 email environment, Kroll recommends updating the application properties in the M365 Azure portal. Navigate to Microsoft Entra ID and then Enterprise Applications; choose the malicious application and then Properties.
Two properties settings will need to be updated to revoke access to the application: Enabled for users to sign in and Visibility to users. Ensure that both options are selected as No (Figure 3). These settings will prevent users from being able to see or sign in to the application.
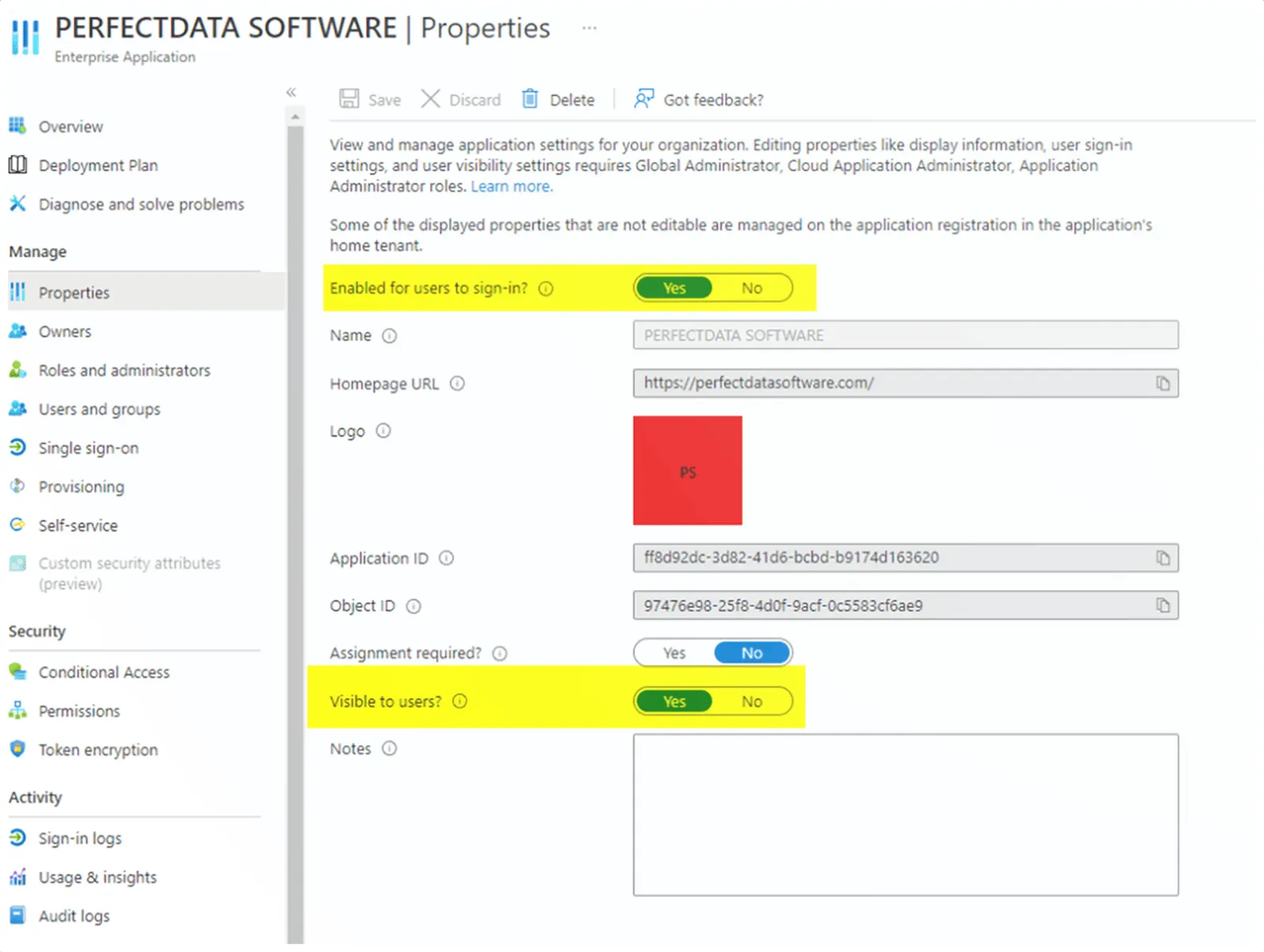
Figure 3 – Remediation of Malicious Enterprise Applications
The default user consent setting is to allow user consent for apps. Therefore, adjusting that setting is a safeguard that can prevent enterprise applications from being installed in an M365 environment. To edit the setting, navigate to the M365 Azure portal, then Microsoft Entra ID, Enterprise Applications, User Settings and User consent settings. Ensure that User consent for applications is set to Do not allow user consent (Figure 4).
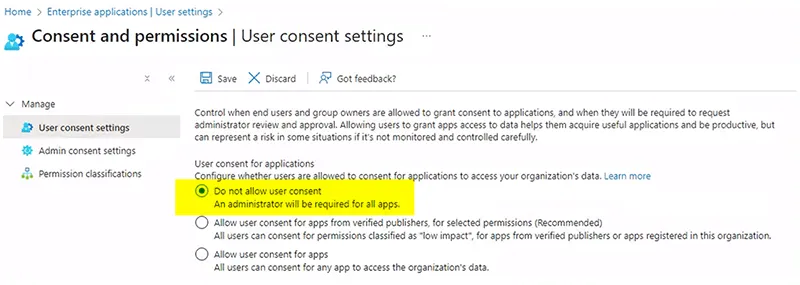
Figure 4 – Enterprise Applications User Consent Settings
M365 has become a powerful productivity and communication tool for businesses, and threat actors have become increasingly efficient at leveraging AiTM attacks to gain access and third-party applications to exfiltrate the entire contents of affected mailboxes. It is critical to monitor for unknown enterprise applications and regularly review security and configurations to safeguard against these threat actor techniques.


